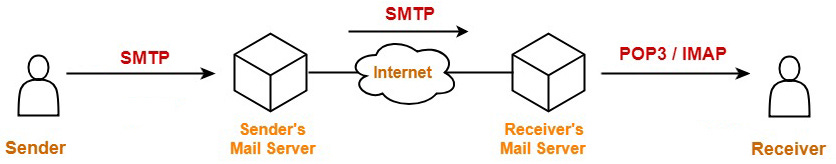
How to know if an email is spam?
Email Security Analysis
In December 2021, 45.37% of total emails were spam emails. According to the latest reports from Talos Intelligence, an surprisingly 84.82% of all emails are spam. 94% of malware is delivered via email.
Several types of cybercrimes are carried out through phishing emails. Every day, everyone of us gets a ton of emails, a large majority of which land in our spam folders. However, phishing emails frequently manage to bypass email client software safeguards and reach our inboxes.
So, if you're wondering how to spot a fake email or, more specifically, how to tell if an email is genuine or fake, keep reading.
Examine the email header information to ensure the sender's address is correct.
An email phishing attack can be identified by the attackers' use of well-known companies or individuals as a cover. The target of the cybercriminal will interact with the email since it appears to be from a real person or company.
Legit companies or organizations usually send email from email addresses that have the company's domain name followed by the "@" symbol. For example, abc@noon.com, abc@amazon.sa, abc@extra.com, etc. In other words, the company domain must follows the "@" symbol. To get such email address, you must own the domain name, or have an authorized person from the company to create one for you.
If you receive an email claiming to be from a reputable organization, here's how you can easily tell if the email is fake:
The sender's email is coming from public domain email addresses like Gmail, Hotmail, Mail, etc.
The email is sent from an unknown domain.
The sender's name and the name in the email address are not the same.
For example, if the sender claims that the email is from Meezan Bank, the sender's email address should contain @meezanbank.com. If the sender's email address ends with "@gmail.com" or some unusual domain name after @, this is a big red flag.
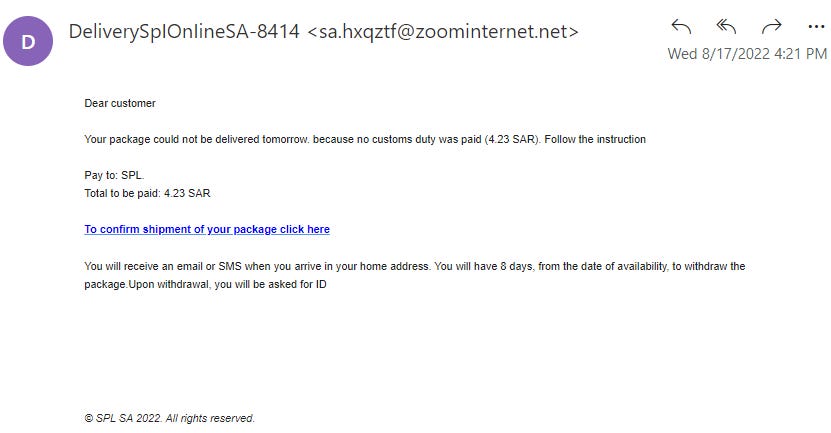
See the following example spam email I recently received:
As you can see in the screenshot above, if the email was from Saudi Post, the sender's email address should not have been from some unknown domain like "@zoominternet.net" instead of "@splonline. com.sa".
See another example below. Here, a spammer impersonates a Saudi Post. But such a fake email is easy to recognize because of the non-company related email address:
Cybercriminals hope that the recipient will forget to check the sender's email address.
In email addresses, look for deceptive domains and spellings.
Some cybercriminals do not use normal email addresses. They buy domain names that resemble the website of the legitimate business they want to impersonate. They usually add additional words or change some letters/words to the original domain name. Check out the table below to understand how fraudsters exploit domains names:
Now, even if email recipients are alert, they may fail to see the difference between support@amazon.sa and support@arnazon.sa. Thus, it is important that you always review the sender's email address with extra caution.
Keep an eye on the use of an email's Bcc field.
In some emails, your email address is listed in the Bcc field rather than the recipient's (To). While there is nothing wrong with including the recipient in the Bcc field, it is uncommon for businesses to do so when communicating with customers. No legitimate company, for example, will send you a blind carbon copy email to verify your account information or request that you download transaction receipts. Because they will make direct contact with you.
So, if you see your email address in the "Bcc" field instead of "To", this is a sign that the email is fake.
Let's consider the phishing email example in the screenshot below. Check that the sender has not entered my email address in the "To" field. Also, added "AL AHLl" to the sender's email address display to trick the me.
Examine whether any embedded links lead to unexpected websites.
Unexpected redirect links are another feature of fake email. Embedded links in emails should take you to the same web page as the link itself. However, scammers include content that appears to take you to a legitimate website, but the hyperlinks they embed take you to a malicious website instead.
For example, suppose you receive an email that appears to be from PayPal. It is informing you of an unauthorized login attempt and requesting that you change your password to protect your account. There is a link to change your password:
https://www.paypal.com/account/passwordChange
Because the link appears legitimate, you believe it is safe to click on it. When you click on that link, however, you will be redirected to a spam website that appears legitimate due to the use of PayPal's site design, colors, fonts, and logo. The fake website will try to trick you into providing your login information or other sensitive information.
Some links may lead users to websites that contain malware, which automatically downloads malware onto users devices without their knowledge. Most malware is distributed via email, according to Verizon's Data Breach Investigation Report (DBIR).
But how can you tell if a link is valid without clicking on it? There are two ways you can check for fake links in suspicious emails:
1. Hover your mouse over the link to display the original URL. Hovering your mouse over the link will reveal where it will take you. If the pop-up URL differs from the information in the link text, it is most likely a malicious link. Please do not click on it!
2. Right-click the in question link (or button) and choose Inspect from the drop-down menu.
You'll see a URL followed by a href= text here. This is the destination of the link. In other words, it means that clicking on the link will take you to that specific URL. You can always inspect suspicious links, media, and buttons by using this technique.
If the links you see use shortened URLs (links that begin with tinyurl, bit.ly, goo.gl, is.gd, t.co, and so on), then you can use this website (getlinkinfo .com) to see the extended URL.
Check for unusual spelling and grammar errors.
If an email has a lot of grammar, spelling, or punctuation errors, that's a red line. Legitimate companies follow email etiquette and editorial standards. While there may be some small errors on occasion, it is unusual to see multiple errors in a single message. Never ignore such mistakes.
Check to see if the language of immediate actions is being used.
Fraudsters attempt to provoke emotional responses such as anger, shock, sympathy, panic, curiosity, and so on. They are more likely to deceive their targets this way.
For example, they may send you emails on the following topics:
An incredible deal/discount on products.
Winning a high-value lottery.
Job offers.
Unauthorize access to your account.
In the event of disclosure of your confidential data.
A (fake) purchase from your account.
Fundraising campaign for the poor suffering from rare diseases/victims of natural disasters.
Email recipients might become emotional over a variety of subjects. Since hackers are aware of this, they will employ email subject lines that persuade recipients to act without carefully reading or researching the email, and will try to respond promptly.
Hackers like to create a sense of urgency. Scammers will occasionally impose deadlines to pressure users into acting fast and hurriedly. Hackers frequently impose a 24- or 48-hour limit. Such deadlines put the user under pressure to execute the advised quick steps in the email.
Consider whether any email attachments are unwanted or unexpected.
Asking yourself, "Did I request this information?" is a solid rule of thumb when it comes to email attachments. In order to mislead you into downloading their harmful executables without your knowledge, fraudsters frequently send emails with phony attachments. These attachments may take many different forms.
Invoice documents.
Payment Receipts.
Photos or other graphics files.
Pricing sheets documents.
Spreadsheets (Excel etc).
Malware that uses documents as its delivery medium is now rather widespread. This is due to the addition of scripting and macros that allow Word and PDF files to function as executables by Microsoft and Adobe.
"Some types of document-based malware can spread to other documents on a compromised system. Once there, malware can spread through any legitimate documents a user sends to friends and colleagues."
Even if the email comes from a legitimate email address, be cautious.
The information provided above will assist you in determining whether or not an email is fraudulent. But what if you get an unexpected or unwanted email from a friend or relative using their legitimate email address?
Malware and cyber-attacks of various types can hack users' devices and send phishing emails on their behalf to other victims. Make use of your instincts. Something in the email may appear "off" - for example, the scammers may ask you to:
Transfer money immediately to help them.
Open the website to take advantage of incredible (unreal) deals/discounts.
Donate money to an unknown organization.
Reply with your phone number, some files or personal information.
Download software, attachments, or media files.
If an email is sent by a friend or relative from a valid email address, the sender should be contacted by phone first. Your friend's or relative's email account may have been hacked and they are unaware of it!
What should you do if the email is fake?
The above mentioned tips will definitely help you in spotting a fake email. But, What to do after receiving spam or fake email? Ignoring such fake emails will not be enough.
Block the sender.
Phishing emails should be deleted immediately.
Report as spam
Report a fake email: If you receive a phishing email from an employee of a company, forward the email to the company's official customer support to report the email address.